Symantec reveals more hack attempts on Swift network
Symantec has found evidence that the Odinaff group has mounted attacks on Swift users, using malware to hide customers’ own records of Swift messages relating to fraudulent transactions.
The tools used are designed to monitor customers’ local message logs for keywords relating to certain transactions. They will then move these logs out of customers’ local Swift software environment. Symantec says it has no indication that Swift network was itself compromised.
Symantec says these Odinaff attacks are an example of another group believed to be involved in this kind of activity, following the Bangladesh central bank heist linked to the Lazarus group.
There are no apparent links between Odinaff’s attacks and the attacks on banks’ Swift environments attributed to Lazarus and the Swift-related malware used by the Odinaff group bears no resemblance to Trojan.Banswift, the malware used in the Lazarus-linked attacks.
But Symantec notes that the attacks involving Odinaff share some links to the Carbanak group, whose activities became public in late 2014. Carbanak also specialises in high-value attacks against financial institutions and has been implicated in a string of attacks against banks in addition to point of sale (PoS) intrusions.
This is bad news for Swift but its fight back against these attacks has been extensive and ongoing. It has spoken strongly on the subject and recently unveiled SwiftSmart modules to help its customers operate their Swift environment “securely and in-line with best practice”. This move is also a “critical part” of its Customer Security Programme launched in May 2016. That five-part plan was a result of various hacking incidents.
It’s not just Swift
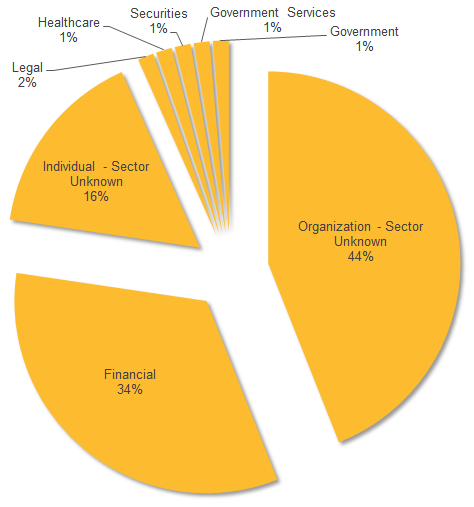
Symantec says that since January 2016, discreet campaigns involving malware called Trojan.Odinaff have targeted a number of financial organisations worldwide. These attacks appear to be “extremely focused” on organisations operating in the banking, securities, trading and payroll sectors. Organisations who provide support services to these industries are “also of interest”.
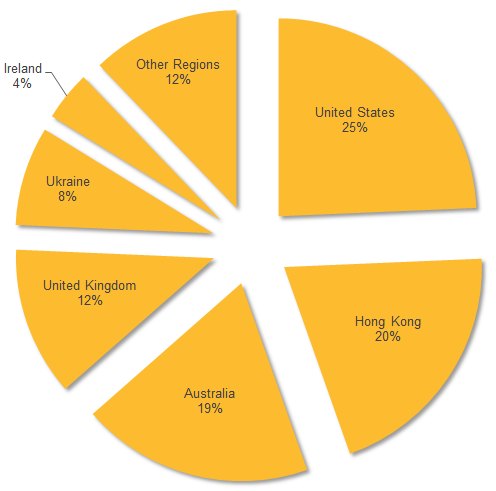
The attacks have hit a wide range of regions, with the US the most frequently targeted. It was followed by Hong Kong, Australia, the UK and Ukraine.